1.为什么需要Ingress
- 我们使用传统的NodePort类型的Service的确能将集群内的服务暴露给集群外部客户端去访问,但是使用这种类型的Service存在以下问题。
- 一个端口只能使用一个服务,所有通过NodePort暴露的端口都需要提前规划;
- 如果集群上的Service的数量太多的话,暴露的NodePort端口不具有连续性。后期维护成本太大,且不宜于管理;
- 无论是Iptables或者是Ipvs模型的Service都配置在Linux内核中的Netfilter之上进行四层调度。是一种比较通用的调度器。支持调度HTTP、Mysql等应用层服务,不过,也正是工作于传输层从而使得它无法做到类似卸载HTTPS中的SSL会话,也不支持基于URL的请求调度机制,因为它工作在传输层。kubernetes也不支持为此类负载均衡配置任何类型的健康状态检测机制。
- 为了解决这种需求,提供了一种高级的流量管理,也就Ingress和Ingress Controller,kubernetes使用Ingress Controller来接收所有入口的流量,然后通过Ingress资源来定义流量如何区分,以及如何转发的规则。有了Ingress和Ingress控制器。我们就可以直接定义流量转发规则来发布服务,而无需创建许多的NodePort和LoadBalancer类型的Service。
- 官方文档: https://kubernetes.io/zh-cn/docs/concepts/services-networking/ingress/
2.什么是Ingress以及Ingress的资源规范
2.1什么是Ingress?
在kubernetes之中,Service资源和Pod资源的IP地址仅能用于集群网络的内部通信,所有的网络流量都无法穿透边界路由器(Edge Router)以实现集群内外通信,尽管可以使用NodePort或者LoadBalancer类型通过节点引入外部流量,但它依然是4层流量转发。
Ingress是kubernetes标准的资源类型,它主要用来定义流量转发规则,但是Ingress资源并不能实现流量的转发以及调度,它仅仅是一组流量路由的规则集合,这些规则要真正发挥作用还需要使用Ingress-Controller,由Ingress-Controller控制器读取对应的Ingress规则,然后完成流量的路由以及转发;
2.2什么是Ingress-Controller?
Ingress Controller可以由任何具有反向代理(HTTP/HTTPS)功能的服务程序实现,如Nginx、Traefik、Envoy、Haproxy。Ingress-Controller通过Pod的形式运行在kubernetes集群上,它能够与集群上的Pod直接通信,这样就可以让用户的流量经过Ingress-Controller直接调度到后端的Pod。
Ingress-Controller类似于Nginx服务,它负责读取Ingress的规则,然后转换将规则转换为nginx.conf配置文件。这样就可以根据对应的规则来实现流量的调度。同时它还会实时感知后端Serrvice对应Pod变化,当Pod发生变动后,Ingress-Controller会再次结合Ingress的规则,进而完成对应配置的动态更新。
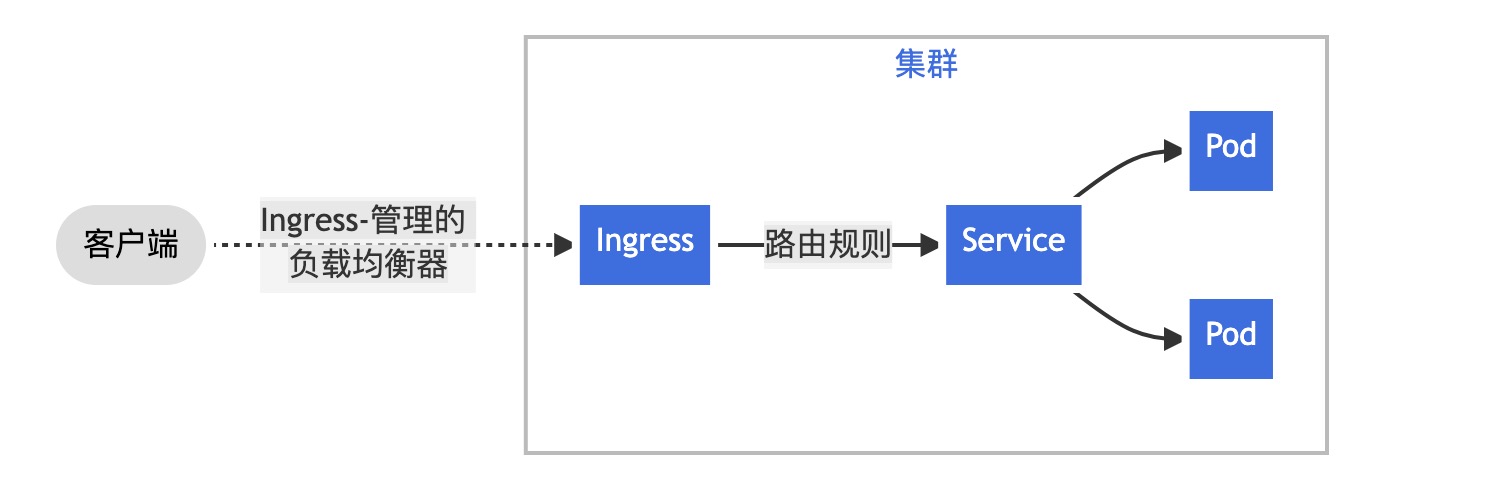
需要注意的是: 使用Ingress资源进行流量分发的时候,Ingress-Controller可基于某个Ingress资源定义的规则将客户端的请求流量直接转发至与Service对应的后端的Pod资源之上。这种机制会绕过Service资源,从而省去了由kube-proxy实现的端口代理开销。实际的访问是Clinet--->Ingress Controller----->通过Ingress规则---->借助Service识别目标有哪些Pod。
2.3Ingress配置资源规范
apiVersion: networking.k8s.io/v1 # 资源所属的API群组和版本
kind: Ingress # 资源类型
metadata: # 元数据
name: <string> # 资源名称
namespace: <string> # 名称空间
spec:
ingressClassName: "nginx" # 适用的Ingress控制器类别,须明确指明
rules: <[]object> # Ingress规则列表
- host: <string> # 虚拟主机的FQDN,俗称域名
http: <object>
paths: <[]object> # 虚拟主机的PATH定义列表
- path: <string> # 匹配以什么开头类似于nginx中的location
pathType: <string> # Prefix前缀匹配,不区分大小写 Exact。精确匹配URL,区分大小写
backend: <object> # 后端
service: <object> #关联后端的Service
name: <string> # 后端Service的名称
port: <object> #后端Service的端口
name: # 端口名称
number: # 端口号
3.Ingress的安装与配置
3.1Ingress-Controller的安装;
Ingress-Controller的GitHub地址: https://github.com/kubernetes/ingress-nginx
Ingress-Nginx的annotaions: https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/annotations/#permanent-redirect
3.1.1下载配置文件
root@ks-master01-10:~# wget https://github.com/kubernetes/ingress-nginx/blob/main/deploy/static/provider/kind/deploy.yaml
3.1.2配置文件如下
有几处需要修改
root@ks-master01-10:~# cat deploy.yaml
apiVersion: v1
kind: Namespace
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
name: ingress-nginx
---
apiVersion: v1
automountServiceAccountToken: true
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- namespaces
verbs:
- get
- apiGroups:
- ""
resources:
- configmaps
- pods
- secrets
- endpoints
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- ""
resourceNames:
- ingress-controller-leader
resources:
- configmaps
verbs:
- get
- update
- apiGroups:
- ""
resources:
- configmaps
verbs:
- create
- apiGroups:
- coordination.k8s.io
resourceNames:
- ingress-controller-leader
resources:
- leases
verbs:
- get
- update
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- create
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-admission
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- secrets
verbs:
- get
- create
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
- namespaces
verbs:
- list
- watch
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- nodes
verbs:
- get
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-admission
rules:
- apiGroups:
- admissionregistration.k8s.io
resources:
- validatingwebhookconfigurations
verbs:
- get
- update
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-admission
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-admission
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: v1
data:
allow-snippet-annotations: "true"
kind: ConfigMap
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-controller
namespace: ingress-nginx
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
ipFamilies:
- IPv4
ipFamilyPolicy: SingleStack
ports:
- appProtocol: http
name: http
port: 80
protocol: TCP
targetPort: http
- appProtocol: https
name: https
port: 443
protocol: TCP
targetPort: https
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
type: NodePort # 修改为ClusterIP
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-controller-admission
namespace: ingress-nginx
spec:
ports:
- appProtocol: https
name: https-webhook
port: 443
targetPort: webhook
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
type: ClusterIP
---
apiVersion: apps/v1
kind: Deployment # Deployment需替换为DaemonSet。使用DaemonSet确保每个节点都部署;
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
minReadySeconds: 0
revisionHistoryLimit: 10
selector:
matchLabels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
strategy:
rollingUpdate:
maxUnavailable: 1
type: RollingUpdate
template:
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
spec:
containers:
- args:
- /nginx-ingress-controller
- --election-id=ingress-controller-leader
- --controller-class=k8s.io/ingress-nginx
- --ingress-class=nginx
- --configmap=$(POD_NAMESPACE)/ingress-nginx-controller
- --validating-webhook=:8443
- --validating-webhook-certificate=/usr/local/certificates/cert
- --validating-webhook-key=/usr/local/certificates/key
- --watch-ingress-without-class=true
- --publish-status-address=localhost
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
- name: LD_PRELOAD
value: /usr/local/lib/libmimalloc.so
image: registry.k8s.io/ingress-nginx/controller:v1.3.0@sha256:d1707ca76d3b044ab8a28277a2466a02100ee9f58a86af1535a3edf9323ea1b5
imagePullPolicy: IfNotPresent
lifecycle:
preStop:
exec:
command:
- /wait-shutdown
livenessProbe:
failureThreshold: 5
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
name: controller
ports:
- containerPort: 80
hostPort: 80
name: http
protocol: TCP
- containerPort: 443
hostPort: 443
name: https
protocol: TCP
- containerPort: 8443
name: webhook
protocol: TCP
readinessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
resources:
requests:
cpu: 100m
memory: 90Mi
securityContext:
allowPrivilegeEscalation: true
capabilities:
add:
- NET_BIND_SERVICE
drop:
- ALL
runAsUser: 101
volumeMounts:
- mountPath: /usr/local/certificates/
name: webhook-cert
readOnly: true
dnsPolicy: ClusterFirst # 替换为优先使用集群内的DNS解析服务
hostNetwork: true # 自行添加,80和443监听在宿主机节点
nodeSelector: # 节点选择器,(选择哪些节点部署Ingress默认所有)
ingress-ready: "true"
kubernetes.io/os: linux
serviceAccountName: ingress-nginx
terminationGracePeriodSeconds: 0
tolerations:
- effect: NoSchedule
key: node-role.kubernetes.io/master
operator: Equal
- effect: NoSchedule
key: node-role.kubernetes.io/control-plane
operator: Equal
volumes:
- name: webhook-cert
secret:
secretName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-admission-create
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-admission-create
spec:
containers:
- args:
- create
- --host=ingress-nginx-controller-admission,ingress-nginx-controller-admission.$(POD_NAMESPACE).svc
- --namespace=$(POD_NAMESPACE)
- --secret-name=ingress-nginx-admission
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.k8s.io/ingress-nginx/kube-webhook-certgen:v1.3.0@sha256:549e71a6ca248c5abd51cdb73dbc3083df62cf92ed5e6147c780e30f7e007a47
imagePullPolicy: IfNotPresent
name: create
securityContext:
allowPrivilegeEscalation: false
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
securityContext:
fsGroup: 2000
runAsNonRoot: true
runAsUser: 2000
serviceAccountName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-admission-patch
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-admission-patch
spec:
containers:
- args:
- patch
- --webhook-name=ingress-nginx-admission
- --namespace=$(POD_NAMESPACE)
- --patch-mutating=false
- --secret-name=ingress-nginx-admission
- --patch-failure-policy=Fail
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.k8s.io/ingress-nginx/kube-webhook-certgen:v1.3.0@sha256:549e71a6ca248c5abd51cdb73dbc3083df62cf92ed5e6147c780e30f7e007a47
imagePullPolicy: IfNotPresent
name: patch
securityContext:
allowPrivilegeEscalation: false
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
securityContext:
fsGroup: 2000
runAsNonRoot: true
runAsUser: 2000
serviceAccountName: ingress-nginx-admission
---
apiVersion: networking.k8s.io/v1
kind: IngressClass
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: nginx
spec:
controller: k8s.io/ingress-nginx
---
apiVersion: admissionregistration.k8s.io/v1
kind: ValidatingWebhookConfiguration
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.3.0
name: ingress-nginx-admission
webhooks:
- admissionReviewVersions:
- v1
clientConfig:
service:
name: ingress-nginx-controller-admission
namespace: ingress-nginx
path: /networking/v1/ingresses
failurePolicy: Fail
matchPolicy: Equivalent
name: validate.nginx.ingress.kubernetes.io
rules:
- apiGroups:
- networking.k8s.io
apiVersions:
- v1
operations:
- CREATE
- UPDATE
resources:
- ingresses
sideEffects: None
root@ks-master01-10:~# kubectl apply -f deploy.yaml
3.1.3查看Ingress-Controller运行是否正常
Pod运行正常,
root@ks-master01-10:~# kubectl get pods -n ingress-nginx
NAME READY STATUS RESTARTS AGE
ingress-nginx-admission-create--1-hcfr2 0/1 Completed 0 2d23h
ingress-nginx-admission-patch--1-6tdvp 0/1 Completed 0 2d23h
ingress-nginx-controller-jtwc6 1/1 Running 4 (18h ago) 2d23h
ingress-nginx-controller-x9psq 1/1 Running 4 (18h ago) 2d23h
3.1.4查看Service
root@ks-master01-10:~# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.96.0.x <none> 443/TCP 14d
nginx-svc ClusterIP 10.96.xx.102 <none> 80/TCP 23m
3.2使用Ingress发布应用
条件1: 创建应用
条件2: 创建Service
条件3: 创建Ingress资源
3.2.1创建应用
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deploy
namespace: default
spec:
replicas: 2
selector:
matchLabels:
app: nginx-test
template:
metadata:
labels:
app: nginx-test
spec:
containers:
- name: nginx
image: nginx:1.16
imagePullPolicy: IfNotPresent
ports:
- name: http
containerPort: 80
查看Pod
root@ks-master01-10:~# kubectl get pods -l app=nginx-test
NAME READY STATUS RESTARTS AGE
nginx-deploy-86cf6979bd-b6fld 1/1 Running 0 2m3s
nginx-deploy-86cf6979bd-pz4s8 1/1 Running 0 2m3s
3.2.2创建Service
Ingress资源仅通过Service资源识别相应的Pod资源获取其IP和端口,而后Ingress控制器即可直接使用各Pod对象的IP地址与它直接进行通信,而不经由Service资源代理和调度,因此Service资源的ClusterIP对Ingress控制器一无所用,不过若集群内的其他Pod客户端需要与其通信,那么ClusterIP还是很有必要;
root@ks-master01-10:~# cat nginx-deploy-svc.yaml
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
namespace: default
spec:
selector:
app: nginx-test
ports:
- port: 80
targetPort: 80
root@ks-master01-10:~# kubectl apply -f nginx-deploy-svc.yaml
service/nginx-svc created
查看Service
root@ks-master01-10:~# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
nginx-svc ClusterIP 10.96.79.102 <none> 80/TCP 4s
可以看到后端的端点是2个nginx的Pod
root@ks-master01-10:~# kubectl describe svc nginx-svc
Name: nginx-svc
Namespace: default
Labels: <none>
Annotations: <none>
Selector: app=nginx-test
Type: ClusterIP
IP Family Policy: SingleStack
IP Families: IPv4
IP: 10.96.79.102
IPs: 10.96.79.102
Port: <unset> 80/TCP
TargetPort: 80/TCP
Endpoints: 192.168.1.72:80,192.168.2.21:80
Session Affinity: None
3.2.3集群内测试
因为是ClusterIP,在集群内访问测试是没有问题的;
root@ks-master01-10:~# curl -I 10.96.79.102
HTTP/1.1 200 OK
Server: nginx/1.16.1
Date: Wed, 24 Aug 2022 05:06:42 GMT
Content-Type: text/html
Content-Length: 612
Last-Modified: Tue, 13 Aug 2019 10:05:00 GMT
Connection: keep-alive
ETag: "5d528b4c-264"
Accept-Ranges: bytesÍ
3.2.4创建Ingress资源发布应用;
通过Ingrees资源的FQDN主机或者URL的路径等类似发布的服务,只有用户的访问请求能够匹配到其.spec.rules.host字段定义的主机才能被相应的规则所处理;
root@ks-master01-10:~# vim nginx-deploy-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-test
namespace: default
spec:
ingressClassName: "nginx"
rules:
- host: haitang.nginx.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-svc
port:
number: 80
root@ks-master01-10:~# kubectl apply -f nginx-deploy-ingress.yaml
ingress.networking.k8s.io/nginx-test created
# 可以已经将Pod识别为后端的端点;
root@ks-master01-10:~# kubectl describe ingress nginx-test
Name: nginx-test
Namespace: default
Address:
Default backend: default-http-backend:80 (<error: endpoints "default-http-backend" not found>)
Rules:
Host Path Backends
---- ---- --------
haitang.nginx.com
/ nginx-svc:80 (192.168.1.72:80,192.168.2.21:80)
Annotations: <none>
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal Sync 8s nginx-ingress-controller Scheduled for sync
Normal Sync 8s nginx-ingress-controller Scheduled for sync
# 查看Ingress资源
root@ks-master01-10:~# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
nginx-test nginx haitang.nginx.com xx.xx.xx.xx 80 13m
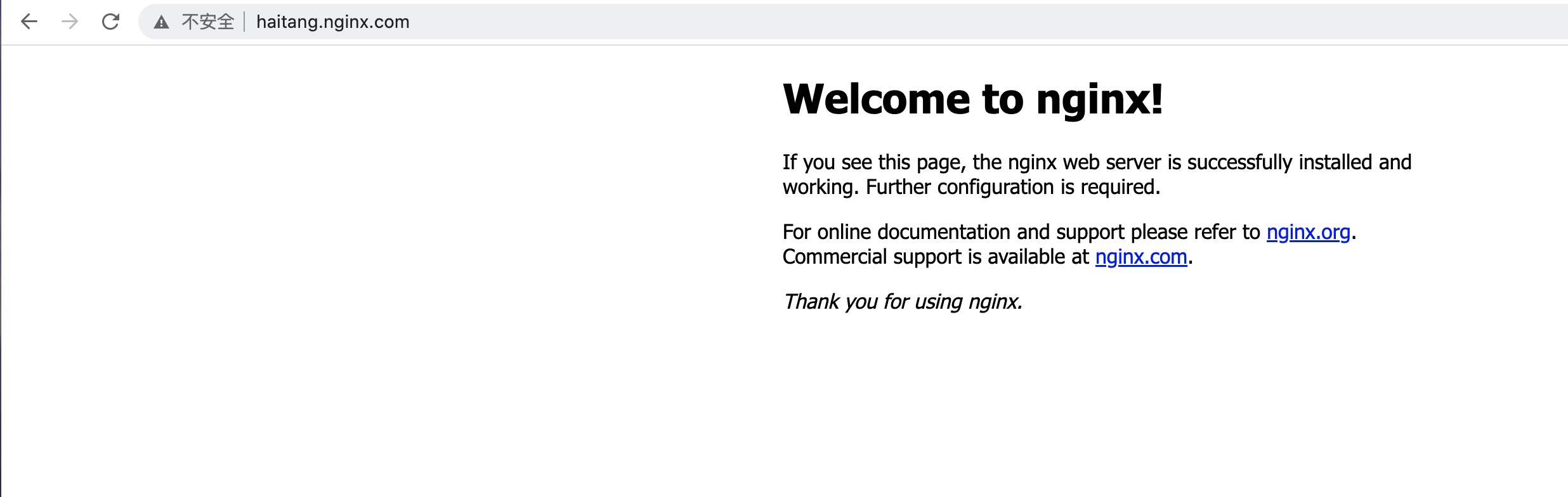
3.2.5集群外测试访问;
需配置/etc/hosts访问即可;
sh-3.2# curl -I haitang.nginx.com
HTTP/1.1 200 OK
Date: Wed, 24 Aug 2022 05:04:15 GMT
Content-Type: text/html
Content-Length: 612
Connection: keep-alive
Last-Modified: Tue, 13 Aug 2019 10:05:00 GMT
ETag: "5d528b4c-264"
Accept-Ranges: bytes
当然网页访问也是没有问题